Encryption Software Market Overview
The global encryption software market size was valued at USD 13.7 billion in 2022 and is projected to reach USD 66.5 billion by 2032, growing at a CAGR of 17.4% from 2023 to 2032.
The rising number of data breaches and increased compliance regulation among the developing nation drive the growth of the market. In addition, the rise in the adoption of cloud and virtualization among enterprises fuels the growth of the market. The widespread adoption of IoT technology & cloud services and ongoing technological advancement in encryption chips are expected to provide lucrative opportunities for the growth of the market.
Key Market Trends & Insights
- By component, the software segment accounted for the largest encryption software market share in 2022.
- By deployment mode, the on-premisesegment accounted for the largest encryption software market share in 2022
- Region-wise, North America generated the highest revenue in 2022.
- Depending on the end-user, the BFSI segment generated the highest revenue in 2022.
Market Size & Forecast
- 2022 Market Size: USD 13.7 Billion
- 2032 Projected Market Size: USD 66.5 Billion
- Compound Annual Growth Rate (CAGR) (2023-2032): 17.4%
What is Encryption Software?
Encryption is one of the fastest emerging data security solutions, which protects confidential data from being accessed by unintended users. The main purpose of encryption is to protect the confidentiality of the data stored in files/folders and disks and data traveling over a wireless network, depending upon the security and compliance needs of the organization.
The report focuses on the growth prospects, restraints, and trends of global encryption software market analysis. The study provides Porter five forces analysis to understand the impact of various factors such as bargaining power of suppliers, competitive intensity of competitors, threat of new entrants, threat of substitutes, and bargaining power of buyers on the global encryption software market.
Encryption Software Market Segment Review:
The global encryption software market is segmented based on component, deployment model, enterprise size, function, industry vertical, and region. In terms of components, it is bifurcated into software and service. Based on the deployment model, the market is segmented into on-premises and clouds. By organization size, it is bifurcated into large enterprises and small and medium-sized enterprises (SMEs). In terms of function, the market is divided into disk encryption, communication encryption, file/folder encryption, and cloud encryption. As per industry vertical, it is classified into BFSI, IT/telecom, government & public, retail, healthcare, aerospace & defense, media & entertainment, and others. Region-wise, it is analyzed across North America, Europe, Asia-Pacific, and LAMEA.
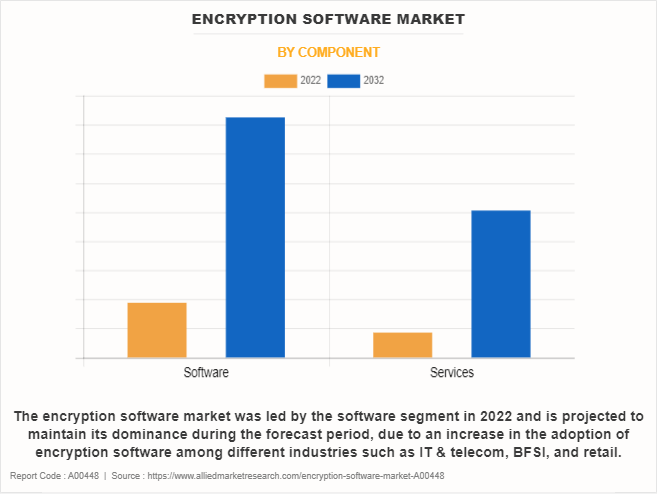
By component, the encryption software market size was led by the software segment in 2022 and is projected to maintain its dominance during the forecast period, due to an increase in the adoption of encryption software among different industries such as IT & telecom, BFSI, and retail. However, the service segment is expected to grow at the highest rate during the forecast period, owing to an increase in the adoption of services among the end users, as they ensure the effective functioning of software and platforms throughout the process, which boosts the global encryption software market.

Region wise, the encryption software market size was dominated by North America in 2022 and is expected to retain its position during the forecast period. This is attributed to expanding mobile wireless network has increased data protection vulnerabilities, making encryption technology an important and necessary component of every organization in the region. However, Asia-Pacific is expected to witness significant growth during the forecast period, owing to presence of numerous storage device manufacturers.
Market Landscape and Trends:
The encryption software market environment and trends around encryption software show a vibrant, changing sector of the economy propelled by the growing demands of several industries for data protection and privacy. Encryption software is essential for protecting data from cyber threats and unauthorised access. Its purpose is to protect sensitive information by transforming it into unintelligible code. The increasing use of cloud-based encryption solutions is a notable trend in the encryption software industry. This trend is fuelled by the growing demand for secure data transfer and storage in cloud environments as well as the expanding popularity of cloud computing.
Furthermore, there is a growing need for encryption solutions designed specifically for mobile platforms to ensure data security on smartphones, tablets, and other portable devices due to the spread of mobile devices and remote work arrangements. Furthermore, the adoption of encryption software by businesses globally is still fuelled by compliance with data protection laws like the CCPA, GDPR, and HIPAA. These laws enforce strict encryption and data security procedures to safeguard private and sensitive data, which in turn promotes market expansion. Furthermore, enterprises are being forced to invest in strong encryption solutions to strengthen their cybersecurity posture and reduce risks to their finances and reputation due to the rising frequency of ransomware attacks, data breaches, and violence.
Top Impacting Factors:
Increase in complexity & volume of data breaches and brute force attacks
- Increase in number of data breaches and brute force attacks owing to rise in digitalization is one of the driving factors of hardware encryption. Brute force attacks are increasing at a rapid pace; therefore, resulting in a strong need for encrypted devices. Most of the companies have started manufacturing encrypted keys/chips with algorithm of 128-bit symmetric key, 256-bit keys that has more security. It is expected that manufacturers would come up with higher algorithm bit keys and generate a higher demand for the same in applications such as healthcare, BFSI, military & aerospace, and few others.
- For instance, in September 2023, Arqit Quantum Inc launched Arqit WalletSecure. Arqit sells a core Symmetric Key Agreement Platform-as-a-Service which can be used for any encryption task and provides a Symmetric Key Agreement upgrade for digital assets used by banks for international payments and for use in global trade finance and NetworkSecure provides a Symmetric Key Agreement upgrade for firewalls and has already been integrated with the products of two market leading firewall vendors. Such hardware-encrypted devices protect number of security threats and offers an effective way to secure privacy of sensitive personal as well as corporate data which fuel the growth of the encryption software industry.
Increased compliance regulations
- The increasing government, as well as state regulations on data privacy and compliance, require enterprises to tighten their data security measures. With the growing number of stringent regulations, organizations need to put in place effective data security technologies, to abide by the applicable laws and ensure that sensitive data or personally identifiable data (PII) about customers is always protected.
- Furthermore, developed geographies such as North America and Europe already have federal-level regulations requiring mandatory compliance with data privacy laws, and developing geographies such as Asia-Pacific and LAMEA, are enacting and implementing more concrete data protection legislation.
- In addition, various countries across the globe have implemented different laws to protect sensitive information which is more susceptible to identity theft or fraud. For instance, the Canadian government launched the Personal Information Protection and Electronic Documents Act (PIPEDA) to protect individuals' privacy rights and requires organizations to obtain consent for the collection and handling of personal data. The obligation to comply with the increasing complexity of such laws has become a key driving force for the adoption of encryption.
Restraints
High capital investment
Large capital investment required for installation as well as maintenance of hardware encryption devices is the major factor impacting negatively on the growth of the encryption software market. The overall installation cost of hardware encryption devices comprises annual maintenance cost, licensing cost, technical cost for password reset, staging cost, pre-provisioning cost, user excess operating cost, and others. Also, updates of the hardware system are only possible through device substitution, which makes it difficult for implementation and increases capital investment.
Limiting the use of encrypted devices in some of the countries
In some countries, using a laptop with encrypted products has become a malpractice, since encryption products are often used for illegal purposes and various terrorist & extortion activities. U.S. has imposed stringent export and import regulations, which have strictly prohibited carrying encrypted devices, while travelling. This could lead to the device being confiscated leading to the person carrying the device being penalized. Thus, it acts as a restraint for the encryption software market growth.
Opportunities
Widespread adoption of Internet of Things (IoT) technology and cloud services
Internet of Things (IoT) device collects and exchanges data over the Internet either with dedicated control units or cloud services. Devices with weak encryption software industry based IoT security are vulnerable to cyberattacks, which put the privacy of organizations and individuals at high risk. Hardware encryption technology used for IoT devices provides the highest level of IoT device security. IoT devices secured by using hardware-based encryption cannot be changed by using any attack, which provides high IoT device security. There is an increase in penetration of IoT devices owing to the adoption of hardware based encrypted devices, which is opportunistic for the encryption software market. For instance, the U.S. is a global leader for IoT spending and is expected to spend almost $194 billion in 2019.
Furthermore, use of cloud computing have led to an increase in data breaches owing to which many enterprises are adopting encryption software to secure their data. In addition, hardware component in the encryption hold sensitive corporate information or customer data, a stolen or lost drive can become a data breach and a privacy violation. Due to which, there is an increase in the need for adopting encrypted devices among the customers.
Key Encryption Software Companies:
The following are the leading companies in the encryption software market.
- Amazon Web Services, Inc. (AWS)
- Check Point Software Technologies
- Cisco System, Inc.
- F-Secure
- Fortinet, Inc.
- IBM Corporation
- Microsoft Corporation
- Oracle Corporation
- Palo Alto Networks, Inc.
- Trend Micro Incorporated BFSI.
Recent Strategic Developments in the Encryption Software Market:
June 15, 2023: Secure-IC partnered with NSITEXE to provide security solutions for Cyber-Physical Systems (CPS). Moreover, SecuryzrTM offers an integrated Security Service Platform (iSSP), which comes with complete security lifecycle management for devices in the field. This includes provisioning secure firmware and cryptographic keys, automated secure onboarding to any platform or multiple platforms simultaneously, and comprehensive security monitoring comprising firmware encryption, signing and secure updates over-the-air, and certificate and key renewal and revocation.
In April 04, 2023, Utimaco acquired German data protection specialist Conpal GmbH and drives strategic expansion of its solution portfolio to provide a complete portfolio for IT security from a single source in the areas of data encryption, hardware security modules, key management and public key infrastructure (PKI) in highly regulated areas. At the same time, the takeover marks another milestone in Utimaco strategic development from a product to a solution provider.
In May 2023, Vaultree significantly improved safeguarding healthcare data by introducing its state-of-the-art, fully functional Data-in-Use encryption solution to the industry. Accompanied by an innovative software development kit and an encrypted chat tool, Vaultree's technology transforms the data encryption landscape. It offers comprehensive protection for sensitive patient data, ensuring its security even during a breach, while maintaining operational efficiency and performance.
Key Benefits for Stakeholders
- This report provides a quantitative analysis of the market segments, current trends, estimations, and dynamics of the encryption software market forecast from 2023 to 2032 to identify the prevailing encryption software market opportunities.
- The encryption software market research is offered along with information related to key drivers, restraints, and opportunities.
- Porter's five forces analysis highlights the potency of buyers and suppliers to enable stakeholders make profit-oriented business decisions and strengthen their supplier-buyer network.
- In-depth analysis of the encryption software market segmentation assists to determine the prevailing market opportunities.
- Major countries in each region are mapped according to their revenue contribution to the global market.
- Market player positioning facilitates benchmarking and provides a clear understanding of the present position of the market players.
- The report includes the analysis of the regional as well as global encryption software market trends, key players, market segments, application areas, and market growth strategies.
Encryption Software Market Report Highlights
| Aspects | Details |
| Market Size By 2032 | USD 66.5 billion |
| Growth Rate | CAGR of 17.4% |
| Forecast period | 2022 - 2032 |
| Report Pages | 280 |
| By Component |
|
| By Deployment Mode |
|
| By Enterprise Size |
|
| By Function |
|
| By Industry Vertical |
|
| By Region |
|
| Key Market Players | Fortinet, Inc., Microsoft Corporation, Cisco System, Inc., Check Point Software Technologies, IBM Corporation, Trend Micro Incorporated, Oracle Corporation, Amazon Web Services, Inc., Palo Alto Networks, Inc., F-Secure |
Analyst Review
Based on numerous interviews that were conducted with top-level CXOs, the adoption of encryption software has increased over time due to the rising adoption of cloud and virtualization in the IT industry and evolving supportive government regulations across the globe. In addition, the ability of software to protect the confidentiality of digital data stored on computer systems or transmitted over the internet is increasing its popularity among end users. Furthermore, many small and medium-sized enterprises are adopting cloud-based encryption software to ensure that organization data is not accessed by any unauthorized user.
According to CXOs of leading companies, the increase in economic strength of developing nations such as China and India, is expected to provide lucrative opportunities for market growth. North America is expected to dominate the market during the forecast period. Moreover, emerging countries in Asia-Pacific and Latin America are projected to offer significant growth opportunities during the forecast period. The global players are focusing on product development and increasing their geographical presence, owing to growth in competition among local vendors, in terms of features, quality, and price. In addition, these players are adopting various business strategies to enhance their product offerings and strengthen their foothold in the market.
For instance, in September 2021, Kanguru collaborated with dubai-based it solutions provider PRO TECHnology to expand local support for Kanguru products and services into the key Middle East region with military-grade Defender® hardware encrypted and trusted USB devices, remote management for USB devices containing sensitive data around the world, and drive duplication equipment. The collaboration is expected to improve product interaction, better service integration, and enhanced threat intelligence in BFSI.
Loading Table Of Content...



