Internet Security Market Overview:
Global Internet security market is expected to garner $46.5 billion by 2021, registering a CAGR of 8.4% during the forecast period 2016-2021. The internet has become an integral part of modern life at every instant. It is convenient to share information, data, messages, applications, etc. over the internet. A person uses the Internet at home, office, restaurants, during travel and many more places. With the increased usage of the Internet, threats are being observed across the world, which at times poses severe impact on system functionality and business operations. In order to protect the computing systems and ensure flawless execution of activities, Internet security solutions are used. Internet is an insecure channel for sharing information, as it is subjective to fraud or intrusion such as phishing. Various methods such as data encryption, firewalls, antivirus, etc. are used for protecting and transferring data over internet. The threat of internet security seems to be rising every day as more and more people and organizations around the globe are connecting to internet through World Wide Web, email, VoIP and other services. These attacks carried out are more sophisticated and keep on evolving as the technology advances.
The major factors driving the internet security market are increased internet usage due to advances in wireless communication technology, internet security offered over cloud services, strict government regulations and increase in online financial activities. Internet security solution finds its application into various industries namely banking financial services and institutions, retail, Telecommunication & IT, Government, manufacturing sector, education, defense, aerospace & intelligence and others.
Different Internet security solutions are available in the market, which are used to secure computing devices viz. routers (hardware), McAfee Internet security (software) solutions, etc. Internet security solutions such as hardware or software firewalls are used to protect individual computing devices or network to help the end users to secure their networks from on-line damaging attacks such as viruses, spywares, malware, etc. The value chain of the Internet security comprises of seven stages, namely analysis, security requirements, and security solutions such as hardware, software and services. Further, designing and implementation of the hardware and software is performed by the companies such as Cisco, Symantec, Kaspersky, etc. that supply Internet security solutions. In addition to this, testing & integration and operation & maintenance are the end stage of the value chain, which are elaborated in their respective sections.
Segment Overview:
On the basis of products and services the market is segmented into software, hardware and service. Software is the highest revenue-generating segment in 2013 and service segment is anticipated to grow with the highest CAGR during forecast period. Based on technology the global internet security market is segmented into authentication technology, access control technology, content filtering and cryptography, Authentication is the highest revenue-generating segment in 2013. Whereas, encryption technology is projected to grow with the highest CAGR during forecast period. The adoption of encryption technology in internet security is mainly due to the increasing internet crimes. The message, text or confidential information sent in a secure codded format which can be decrypted only by the user who has the key for decrypting it.
Top factors Impacting Internet Security Market
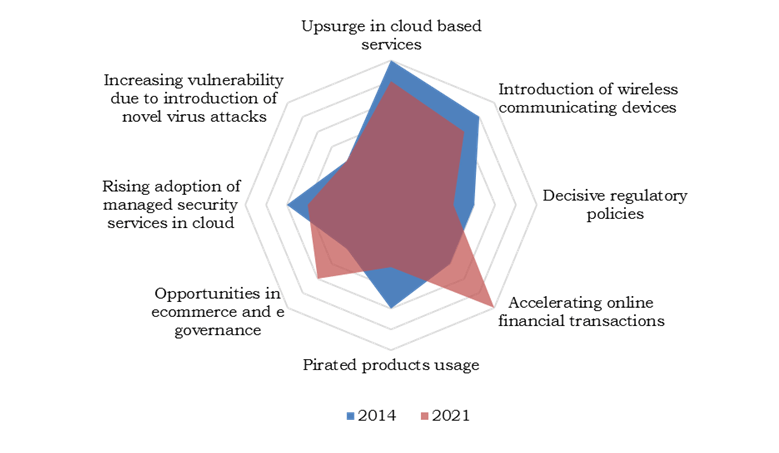
Upsurge in cloud usage
Enterprises use cloud-based services in order to execute business operations smoothly. Such cloud-based services’ usage primarily drives the adoption of Internet security solutions. The multi-national nature of business would further increase cloud-based business operations. However, due to emergence of technologies such as BYOD, the dependence on enterprises’ resources would be reduced by 2020. Furthermore, the contribution from individual users would increase significantly, which would reduce the relative revenue contribution from this factor.
Wireless services' usage
Due to wireless mode of communication, using the Internet is becoming simpler. The efficient wireless network has facilitated data communication to greater extent, which is vulnerable to enormous threats. With rapid uptake of wireless communications, the market also experiences increased acceptance. The rapid increase of mobile data users is influencing the market at greater extent at present. However, over the period rise in mobile data users would be relatively smaller, which in turn would partially diminish impact of this factor on the adoption of internet security solutions
Decisive regulatory policies
Regulations & policies make it mandatory to install Internet security solutions in business organizations. To secure confidence among users, several companies comply with recognized security policies such as OECD principles, etc. Over the forecast period, with maturing regulations, the implications arising out of non-adherence to regulatory policies would reduce.
Impact of COVID-19 on Internet Security Market:
- The growth of the internet security market is expected to increase during the Covid-19 pandemic outbreak. The incidence of cyber-attack in all industries has been increased during the lockdown. Therefore, the adoption of the internet security services and software has been increased in all industries.
- Moreover, work from home facility has been provided in all possible industries and the all organizations are very much conscious about the data and the credentials of files during this pandemic. Therefore, provide the secure and safe network to the employees in work from home facility, the demand for internet security services has been increased.
Key benefits
- The study features extensive research of the internet security market and illustrates the current and future orientation of its market position
- The report provides a current market scenario with a forecast through 2014-2020, considering 2013 as the base year
- A detailed analysis of market segments measures the potential of market. These segments outline the favorable conditions for growth of the NFC systems market
- The report covers an in-depth analysis of the key factors influencing the NFC systems market
- Porters Five Forces model is used to analyze the potency of buyers & suppliers, and highlight the competitive structure of the market, to enable the market players in developing effective strategies
- Industry Value chain analysis highlights the key intermediaries involved and elaborates their roles and value addition at every stage in the chain
Internet Security Market Report Highlights
| Aspects | Details |
| By Products And Services |
|
| By Technology |
|
| By Application |
|
| By Geography |
|
| Key Market Players | Intel Corporation (McAfee, Inc.), Google Incorporation, Kaspersky Lab, Dell (SonicWall, Inc.), International Business Machine (IBM) Corporation, Trend Micro, CISCO Systems Inc., Symantec Corporation, Hewlett Packard (HP) Company, Microsoft Corporation |
Loading Table Of Content...