Hardware Secure Module (HSM) Adapters Market Research, 2031
The global hardware secure module (HSM) adapters market was valued at $1.3 billion in 2021, and is projected to reach $4.4 billion by 2031, growing at a CAGR of 13% from 2022 to 2031. Hardware security module (HSM) adapters are devices that enable the use of an external HSM with a system or application. An HSM is a physical computing device that safeguards and manages digital keys for strong authentication and provides crypto processing. HSMs are often used to secure transactions and communications in financial, government, and other organizations that handle sensitive information.
An HSM adapter connects to the system or application and communicates with the external HSM to offload security-critical functions such as encryption, decryption, and signing. This can help to protect against attacks on the system or application and ensure the integrity and confidentiality of sensitive data. HSM adapters are often used in conjunction with other security measures such as firewalls and intrusion detection systems. They may be provided as a separate hardware device or implemented as a software component.

The hardware secure module (HSM) adapters market size is expected to witness notable growth during the forecast period, owing to a surge in cyberattacks, increasing adoption of cloud-based services, and an increase in preference for digital payments. Moreover, technological advancements in Internet of Things (IoT), the rise in the demand for hardware security modules as 5G becomes mainstream in the hardware secure module (HSM) adapters market, are expected to provide lucrative opportunities for the hardware secure module (HSM) adapters market growth during the forecast period. On the contrary, vulnerability to security data breaches and the need for regular upgrading and maintenance are some of the restraints for the hardware secure module (HSM) adapters market share during the forecast period.
Segment Overview
The hardware secure module (HSM) adapters market is segmented into Type and Industry.
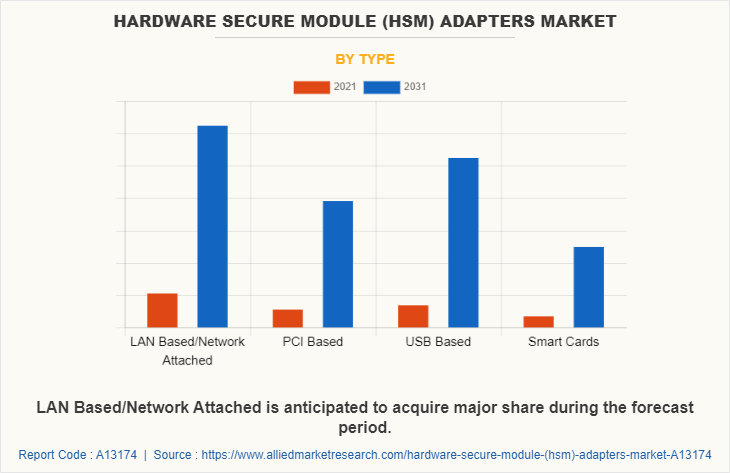
Based on type, the market is divided into LAN-based/network-attached, PCI-based, USB-based, and smart cards. In 2021, the LAN-based/network-attached segment dominated the market in terms of revenue, USB-based segment will acquire major market share till 2031.
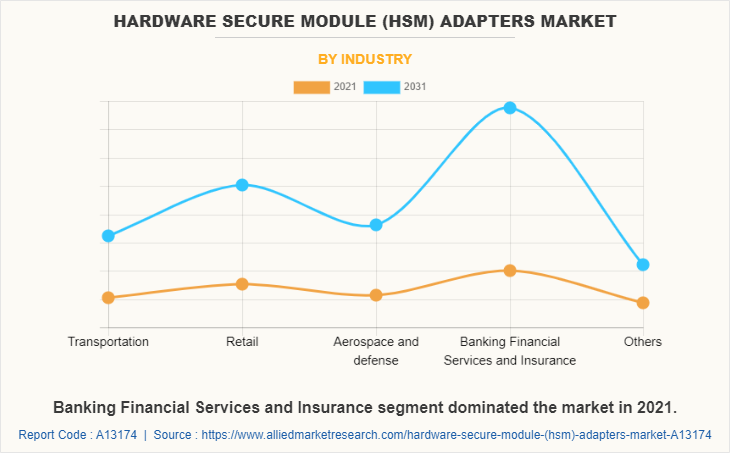
Based on industry, the hardware secure module (HSM) adapters market is segregated into transportation, retail, aerospace and defense, Banking, Financial Services and Insurance, and others. The Banking, Financial Services, and Insurance segment acquired the largest share in 2021 and is expected to grow at a significant CAGR from 2022 to 2031.
Region-wise, the hardware secure module (HSM) adapters Market trends are analyzed across North America (the U.S., Canada, and Mexico), Europe (UK, Germany, France, and Rest of Europe), Asia-Pacific (China, Japan, India, South Korea, and Rest of Asia-Pacific), and LAMEA (Latin America, Middle East, and Africa). Europe and the Asia-Pacific remain significant participants in the hardware secure module (HSM) adapters market.
Competitive Analysis
Competitive analysis and profiles of the major global hardware secure module (HSM) adapters market players that have been provided in the report include Atos SE, Hewlett-Packard Enterprise Development LP, Infineon Technologies, International Business Machines Corporation, Microchip Technology, Securosys, Spyrus, Thales, Utimaco, and Yubico.
Country Analysis
Country-wise, the U.S. acquired a prime share in the hardware secure module (HSM) adapters market forecast in the North American region and is expected to grow at a significant CAGR during the forecast period of 2022-2031. Canada holds a dominant position in the hardware secure module (HSM) adapters market, owing to the rise in investment by prime vendors to boost hardware secure module (HSM) adapters solutions.
In Europe, the UK dominated the hardware secure module (HSM) adapters market outlook, in terms of revenue, in 2021, and is expected to follow the same trend during the forecast period. However, Germany is expected to emerge as the fastest-growing country in Europe's hardware secure module (HSM) adapters with a CAGR of 15.11%, owing to significant development in the retail, industrial manufacturing, IT, and computing sectors, and other sectors in the country.
In the Asia-Pacific region, China is expected to emerge as a significant market for the hardware secure module (HSM) adapters industry, owing to a significant rise in investment by prime players and government institutions in security solutions in the region to save from cyber attacks and data breaches.
In the LAMEA region, the Latin America countries garnered a significant hardware secure module (HSM) adapters market share in 2021. The LAMEA hardware secure module (HSM) adapters market has been witnessing improvement, owing to the growing inclination of companies towards research and development for enhanced connectivity for consumer electronics and telecommunication across this region. Moreover, the Middle East region is expected to grow at a high CAGR of 11.3% from 2022 to 2031, owing to new developments and investments towards building security systems for public transport, banking sectors and other useful things in the region, which is expected to reshape the growth of hardware secure module (HSM) adapters market in the Latin America.
Key Developments/ Strategies
Atos SE, Hewlett-Packard Enterprise Development LP, Infineon Technologies, International Business Machines Corporation, Microchip Technology, Securosys, Spyrus, Thales, Utimaco, and Yubico are the top companies holding a prime share in the hardware secure module (HSM) adapters market. Top market players have adopted various strategies, such as product launch, acquisition, innovation, partnership, and others, to expand their foothold in the hardware secure module (HSM) adapters market.
- In February 2022, Thales announced the launch of Pay Shield 10K technology, which helps to deliver Microsoft Azure Payment Hardware Security Module (HSM), a new service that provides cryptographic key operations to protect real-time, critical payment transactions in Azure. The solution is in public preview and allows service providers and financial institutions to accelerate the digital transformation of their cloud-based payment systems confidently.
- In June 2022, Thales collaborated with NAVER Cloud to launch the first Korean sovereign cloud HSM as-a-service powered by Thales' industry-leading Luna Network Hardware Security Module. The new service helps businesses meet the strict regulatory and industry mandates for control of their data and encryption as they transition from on-premises environments to cloud or hybrid environments.
- In November 2019, Utimaco GmbH launched Block-safe, a new hardware security module (HSM) designed for use with blockchain-based platforms that feature distributed ledger technology. An HSM is crucial to securing blockchain systems to cryptographically protect the information stored in them, maintain information integrity, and ensure audit compliance. Block-safe enables companies to generate, manage, and protect cryptographic keys for blockchain applications.
- In July 2019, Utimaco GmbH and ISARA Corporation, the world’s leading provider of agile quantum-safe security solutions, collaborated to launch the world’s first commercial quantum-safe hardware security module to secure data and infrastructure against an attack by a quantum computer.
- In February 2020, Utimaco GmbH acquired cryptographic key management firm Geobridge Corporation for an undisclosed price. Geobridge was founded in 1997. It sells and supports encryption, cryptography, and payment applications for payment processors, issuers, terminal manufacturers, and merchants.
- In January 2019, Microchip Technology Inc. partnered with The Things Industries and launched the industry’s first end-to-end security solution that adds secure, trusted, and managed authentication to LoRaWAN devices at a global scale. The solution brings hardware-based security to the LoRa ecosystem, combining the MCU- and radio-agnostic ATECC608A-MAHTN-T CryptoAuthentication device with The Things Industries’ managed join servers and Microchip’s secure provisioning service.
- In March 2022, Microchip Technology Inc. launched TrustFLEX ECC608 and Trust Anchor TA10, Qi 1.3 compatible hardware security modules (HSMs). The TrustFLEX ECC608 is an industrial-grade product with a pre-configured key for Qi 1.3 authentication, while the TA 100 is a CryptoAutomotive security IC developed for automotive security applications. Both the ICs provide support for secure boot and multiple key management protocols such as Transport Layer Security (TLS).
- In October 2021, Infineon Technologies launched the SLS37 V2X hardware security module (HSM), a plug-and-play security solution for vehicle-to-everything communication (V2X). The SLS37 V2X HSM is based on a highly secure, tamper-resistant microcontroller tailored to the security needs in V2X applications within telematics control units. It is protecting the integrity and authenticity of messages, as well as the privacy of the sender.
- In January 2021, Securosys and RIDDLE&CODE, an innovative European provider of secure infrastructure and technology, made a strategic partnership. The partnership includes the provision of Securosys HSMs for RIDDLE&CODE's Token Management Platform (TPM). The Token Management Platform is the next generation of RIDDLE&CODE's banking-grade digital asset management solution. Operating in a secure cloud infrastructure, it delivers scalable and flexible custodial and tokenization services to the financial, energy, and metal industries in Europe.
Key Benefits for Stakeholders
- This report provides a quantitative analysis of the hardware secure module (HSM) adapters market segments, current trends, estimations, and dynamics of the hardware secure module (HSM) adapters market from 2021 to 2031 to identify the prevailing hardware secure module (HSM) adapters market opportunities.
- The market research is offered along with information related to key drivers, restraints, and opportunities.
- Porter's five forces analysis highlights the potency of buyers and suppliers to enable stakeholders to make profit-oriented business decisions and strengthen their supplier-buyer network.
- In-depth analysis of the hardware secure module (HSM) adapters market segmentation assists in determining the prevailing hardware secure module (HSM) adapters market opportunities.
- Major countries in each region are mapped according to their revenue contribution to the global market.
- Market player positioning facilitates benchmarking and provides a clear understanding of the present position of the market players.
- The report includes the analysis of the regional as well as global hardware secure module (HSM) adapters market trends, key players, market segments, application areas, and market growth strategies.
Hardware Secure Module (HSM) Adapters Market Report Highlights
| Aspects | Details |
| Market Size By 2031 | USD 4.4 billion |
| Growth Rate | CAGR of 13% |
| Forecast period | 2021 - 2031 |
| Report Pages | 335 |
| By Type |
|
| By Industry |
|
| By Region |
|
| Key Market Players | Infineon Technologies, Atos SE, spyrus, International Business Machines Corporation, Securosys, Utimaco GmbH, Thales, Yubico, Hewlett Packard Enterprise Development LP, Microchip Technology Inc. |
Analyst Review
The global hardware secure module (HSM) adapters market is expected to witness significant growth due to increase in demand for hardware secure module adapters for sectors such as healthcare, IT and computing, BFSI and others.
The increase in adoption of cloud-based services and rise in preference for digital payments, are expected to propel the worldwide hardware secure module (HSM) adapters market expansion during the forecast period. However, vulnerability to security data breaches is expected to restrain market expansion, during the forecast period.
Furthermore, the market for HSMs and other types of security hardware is generally expected to grow in the coming years due to increase in concerns about cyber security threats and the need to protect sensitive data. HSMs are used to secure a variety of applications and processes, including online transactions, credit card processing, and the protection of cryptographic keys, and the growing reliance on these types of applications is likely to drive demand for HSMs and HSM adapters. It is worth noting that the market for HSMs and HSM adapters may be influenced by a number of factors, including technological advancements, changes in regulatory requirements, and shifts in demand for specific types of applications.
HSMs are used to secure a wide range of applications and systems, including online banking systems, payment processing systems, and cloud-based applications. They can be used to secure communication channels, such as VPNs or SSL/TLS connections, and can support various cryptographic algorithms and protocols, such as RSA, ECC, and AES.
As 5G becomes more widely adopted, there is likely to be an increase in the demand for HSMs to secure the various applications and systems that will be using it. This is because 5G is expected to support a much larger number of devices and a wider range of applications than previous generations of wireless technology, and will require a higher level of security to protect against cyber threats and other types of attacks. In addition, the increased speed and capacity of 5G networks is likely to increase the demand for HSMs to secure data transmitted over these networks, as the volume of data being transmitted is expected to significantly increase.
Increase in adoption of cloud-based services and digital payments are the upcoming trends of hardware secure module (HSM) adapters market in the world.
BFSI is the leading application of hardware secure module (HSM) adapters market.
Asia-Pacific is the largest regional market for hardware secure module (HSM) adapters.
The hardware secure module (HSM) adapters market was valued at $1,319.27 million in 2021.
Atos SE, Hewlett Packard Enterprise Development LP, Infineon Technologies, International Business Machines Corporation, Microchip Technology, Securosys, Spyrus, Thales, Utimaco, and Yubico are the top companies to hold the market share in hardware secure module (HSM) adapters.
Loading Table Of Content...



