Cybersecurity Market Overview
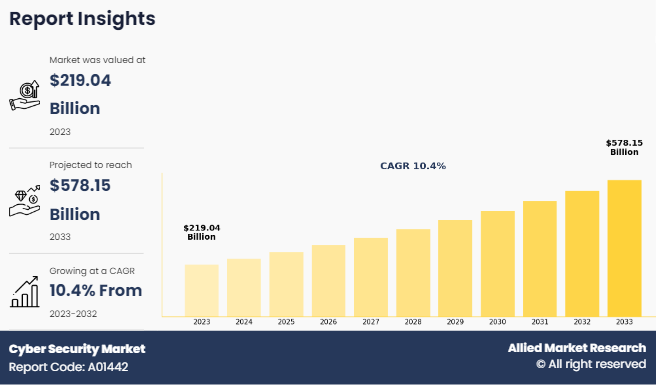
The global cybersecurity market size was valued at USD 219 billion in 2023 and is projected to reach USD 578.2 billion by 2033, growing at a CAGR of 10.4% from 2024 to 2033. The companies harnessing AI and ML improve the security offerings and gain a competitive edge, positioning themselves to capture a larger share of the rapidly growing cybersecurity market.
Key Market Insights
By offering, the solution segment held the largest share in the cyber security market size for 2023.
By deployment, the cloud segment held the largest share in the cybersecurity market for 2023.
By industry vertical, the BFSI segment held the largest share in the cybersecurity market for 2023.
By enterprise size, the large enterprises segment held the largest share in the cybersecurity market for 2023.
Asia-Pacific is expected to witness the highest CAGR during the cyber security market forecast period.
Market Size & Forecast
- 2033 Projected Market Size: USD 578.2 Billion
- 2023 Market Size: USD 219 Billion
- Compound Annual Growth Rate (CAGR) (2024-2033): 10.4%
- North America: Dominated market share during forecast period
- Asia-Pacific: Highest CAGR during the forecast period
What is Cybersecurity
Cybersecurity refers to the activity of securing systems, networks, and data from cyber-attacks, unwanted access, or damage. It involves implementing a range of technologies, processes, and controls to safeguard sensitive information from cyber threats such as hacking, malware, ransomware, and phishing. In addition, cybersecurity involves multiple layers of protection across devices, networks, programs, and data, ensuring confidentiality, integrity, and availability to safeguard sensitive information and maintain system reliability. Moreover, cybersecurity requires continuous monitoring, timely updates, employee training, and the use of encryption, firewalls & authentication mechanisms to ensure robust protection against potential threats.
The rise in remote work trend and BYOD (Bring Your Own Device) policies drives the growth of the cybersecurity market. The employees work remotely and use personal devices to access company networks due to which the organizations face heightened security risks, driving the demand for stronger cybersecurity solutions. In addition, personal devices often lack the security measures of corporate systems, making them more vulnerable to cyberattacks. This shift has increased the cyber security market demand for strong security solutions such as VPNs, endpoint security, and secure access service edge (SASE) platforms to protect sensitive data and ensure the safety of corporate networks in remote work environments, thereby driving the cyber security market growth. However, the high implementation costs pose a significant barrier to the cybersecurity growth. Cybersecurity solutions often require substantial financial investments, including software licenses, specialized hardware, and ongoing maintenance. These financial expenses hamper market growth.
However, implementing Artificial Intelligence (AI) and Machine Learning (ML) in cybersecurity significantly enhances threat detection and response capabilities. These technologies analyze vast amounts of data in real time, identifying patterns that indicate potential security breaches. AI-driven solutions automate responses to threats, reducing response times and minimizing damage.
Cyber Security Market Segment Review
The cyber security market share is segmented into offering, deployment, industry vertical, enterprise size, and region. By offering, the market is classified into solutions and services. The solution segment is further categorized into network security, application security, endpoint security, infrastructure security, and others. The service segment is further segregated into professional service and managed service. By deployment, it is divided into on-premises and clouds. By industry vertical, it is fragmented into IT & telecom, automative, BFSI, government, healthcare, energy & utilities, manufacturing, retail, and others. By enterprise size, it is classified into large enterprises and small & medium enterprises. Region wise, it is analyzed across North America, Europe, Asia-Pacific, and LAMEA.
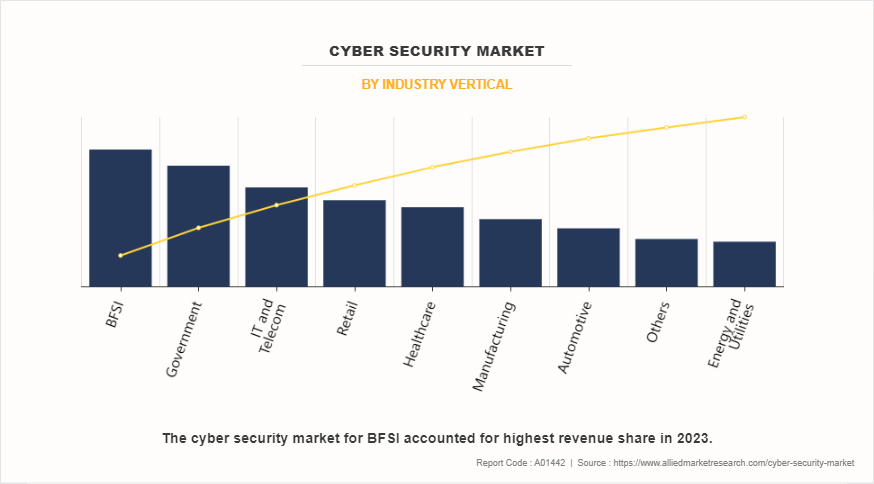
On the basis of industry vertical, it is segmented into IT & telecom, automative, BFSI, government, healthcare, energy & utilities, manufacturing, retail, and others. The global cybersecurity market share was dominated by the BFSI segment in 2023, owing to the critical need for safeguarding sensitive financial data and transactions from cyber threats. However, healthcare segment is expected to register the highest CAGR during the forecast period, owing to increase in digitization of health records and the rise in adoption of telemedicine and connected medical devices drives the demand for cybersecurity solutions.
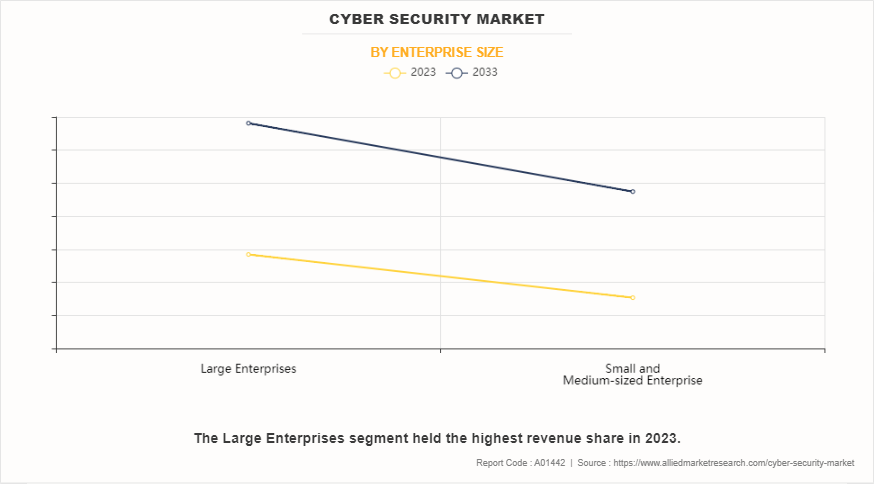
On the basis of enterprise size, it is classified into large enterprises and small & medium enterprises. The large enterprises segment dominated the cybersecurity market share in 2023 and is expected to register the highest CAGR during the forecast period. This was attributed to large organizations facing a higher volume of cyber threats due to their extensive networks and vast amounts of sensitive data, prompting them to prioritize robust security measures.
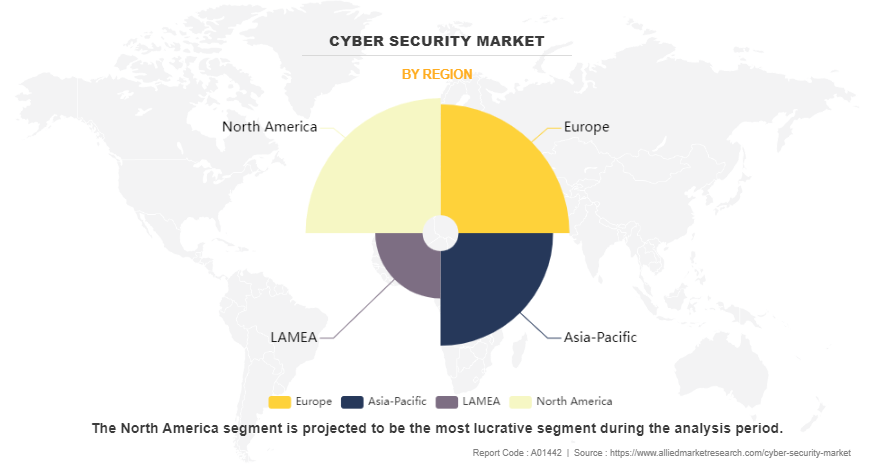
Cyber security market overview region wise, the cybersecurity market share was dominated by North America in 2023 and is expected to retain its position during the forecast period owing to increase in number of cyber threats, robust technological advancements, and substantial investments in cybersecurity solutions by both private and public sectors, enhancing overall security measures, which drives the cybersecurity market growth in the region. However, Asia-Pacific is expected to register the highest CAGR during the forecast period, owing to rapid digital transformation, increase in internet penetration, and rise in awareness of cyber threats. In addition, governments implement stricter regulations, further boosting demand for advanced cybersecurity solutions in the region.
What are the Top Impacting Factors in Cyber Security Market
Key Market Drivers
Rise in number of Cyber Threats
The rise in number of cyber threats drives the cybersecurity market growth owing to the increase in need for organizations to protect sensitive data and ensure the integrity of their digital operations. With the rapid expansion of digital infrastructures, businesses become more vulnerable to cyberattacks, ranging from data breaches to ransomware. This escalation in cyber risks compelled companies to invest significantly in robust cybersecurity solutions to mitigate potential threats. In addition, industries such as banking, healthcare, and government institutions handle vast amounts of confidential information, making them prime targets for cybercriminals, which is expected to drive the demand for enhanced security measures.
For instance, in 2024, Comcast Business Cybersecurity Threat Report became a pivotal resource in shaping the cybersecurity market by delivering comprehensive insights into current threats and vulnerabilities. By analyzing an unprecedented 29 billion cybersecurity events detected in 2023, the report emphasizes the evolving nature of cyber threats and highlights the urgent need for organizations to boost their defenses. The identification of pressing threats empowers businesses to prioritize their cybersecurity investments and strategies, fostering a proactive approach to risk management. This demand for advanced cybersecurity solutions, driven by the insights from the report, stimulates cybersecurity growth as organizations increasingly seek innovative technologies & services to protect their digital assets, enhance incident response capabilities, and ensure compliance with regulatory standards.
Restraint
High Implementation Costs and A Shortage of Skilled Professionals
The rise in costs associated with cybersecurity expertise driven by increase in complexity of cyber threats necessitates demand for advanced technologies and specialized skills, leading to higher expenditures on both tools and personnel. For instance, according to the Center for Security and Emerging Technology, there is a significant shortage of qualified cybersecurity professionals in the U.S., with approximately 700,000 unfilled positions. These challenges are exacerbated by emerging trends in cybersecurity market, such as the shift toward real-time monitoring and predictive analytics to address evolving threats. Thus, there is a shortfall in cybersecurity professionals, which limits market growth.
In addition, the rapid evolution of cyber threats means that organizations require continuous training and real-time threat analysis capabilities, which adds to the financial burden. This combination of heightened demand for skilled workers, the need for sophisticated technology, and ongoing education creates a challenging landscape
Opportunity
Emerging Technologies in Cybersecurity
Emerging technologies in cybersecurity present significant opportunities for cybersecurity market growth by enhancing threat detection, prevention, and response capabilities. Technologies including Artificial Intelligence (AI) and Machine Learning (ML) enhance threat detection and response capabilities by analyzing large data sets for patterns. Other notable advancements include Behavioral Biometrics, which monitors user interactions to identify anomalies, and Zero Trust Architecture, a model that mandates strict verification for all network access.
In addition, technologies such as Blockchain offer secure data storage solutions, while cloud security measures protect data in cloud environments through encryption and multi-factor authentication. As the cybersecurity market continues to grow, these innovations are essential for organizations aiming to fortify their defenses against an ever-evolving threat landscape, emphasizing the necessity of staying updated with the latest cybersecurity technologies to safeguard sensitive information and maintain business integrity.
Furthermore, the proliferation of the Internet of Things (IoT) and edge computing creates new security challenges and opens avenues for developing advanced security measures specifically tailored for these technologies. Solutions designed to protect IoT devices and networks are increasingly in demand as more organizations adopt connected technologies. The surge in emphasis on cybersecurity training and awareness programs is another emerging opportunity for market expansion. Overall, the integration of these emerging trends in cyber security market is poised to drive innovation and expansion within the cybersecurity market, as organizations strive to fortify their defenses against evolving threats.
What are the Leading Companies in Cybersecurity
The following are the leading companies in the cyber security market. These players have adopted various strategies to increase their market penetration and strengthen their position in the cybersecurity industry.
Palo Alto Networks, Inc.
Cisco Systems, Inc.
CrowdStrike, Fortinet, Inc.
Check Point Software Technologies Ltd.
Trend Micro Incorporated.
IBM Corporation, Broadcom Inc.
F5, Inc.
Proofpoint, Inc.
HCL Technologies Limited
Infosys Limited
L&T Technology Services Limited
TATA Consultancy Services Limited
Tech Mahindra Limited
Wipro Limited
Thales S.A.
RSA Security LLC
SonicWall
CyberArk Software Ltd.
Which New Products have Been Launched in the Cybersecurity Sector
In July 2023, IBM launched a new AI-powered cybersecurity solution aimed at improving threat intelligence and reducing response times for large enterprises, enhancing their ability to defend against increasingly sophisticated cyberattacks.
In March 2023, the UK’s National Cybersecurity Centre (NCSC) launched a new program to combat the rise in ransomware attacks across the country, focusing on increasing awareness and offering businesses tools to strengthen their digital defenses.
In April 2023, China implemented new data security laws requiring companies to strengthen their cybersecurity measures, particularly for cloud-based systems and digital transactions. The government began investing in AI-powered cybersecurity tools to address the surge in number of cyberattacks targeting the nation’s infrastructure.
In February 2023, Saudi Arabia hosted the Global Cybersecurity Forum, where it announced new cybersecurity initiatives, focusing on improving cybersecurity awareness and expanding its cyber defense capabilities, particularly in the oil and gas sector.
What are the Key Benefits for Stakeholders
This report provides a quantitative analysis of the market segments, current trends, estimations, and dynamics of the cybersecurity market analysis from 2023 to 2033 to identify the prevailing cyber security market opportunities.
The cybersecurity market research is offered along with information related to key drivers, restraints, and opportunities.
Porter's five forces analysis highlights the potency of buyers and suppliers to enable stakeholders make profit-oriented business decisions and strengthen their supplier-buyer network.
In-depth analysis of the cyber security market segmentation assists to determine the prevailing market opportunities.
Major countries in each region are mapped according to their revenue contribution to the global cybersecurity market.
cybersecurity market player positioning facilitates benchmarking and provides a clear understanding of the present position of the market players.
The report includes the analysis of the regional as well as global cyber security market trends, key players, market segments, application areas, and cyber security growth strategies.
Cyber Security Market Report Highlights
| Aspects | Details |
| Forecast period | 2023 - 2033 |
| Report Pages | 300 |
| By Component |
|
| By Deployment Model |
|
| By Enterprise Size |
|
| By Industry Vertical |
|
| By Region |
|
| Key Market Players | IBM Corporation, Cisco Systems, Inc., Palo Alto Networks, Amazon Web Services, Inc., Rapid7, Inc., Oracle Corporation, Trend Micro Incorporated, Microsoft Corporation, Check Point Software Technologies Ltd., Fortinet, Inc. |
Analyst Review
Cyber security embraces the safety of assets from cyber-crime, cyber threats and other network service interruptions that affect day-to-day operations. Securing IT infrastructure and devices in organizations can be accomplished through active monitoring, exposure of malicious movement, and immediate response to disruptions. Moreover, increase in malware and phishing threats and increase in adoption of IoT and bring your own device (BYOD) trend among organizations is mainly driving the cyber security market growth. Furthermore, increasing need for robust authentication techniques is also expected to provide lucrative opportunities for the market. Moreover, many enterprises integrate cyber defense with traditional security activities, such as personnel and physical security as part of an overarching effort to defend business operations from both internal and external threats. Furthermore, cyber security activities are now being prioritized and aligned for strategic business activities to minimize the damage of IT resources. In addition, according to Netcraft’s web server survey in October 2018, currently there are more than 1.6 billion websites worldwide and more complex ransomware attacks are anticipated to arise in upcoming years. Thus, this is expected to create major growth opportunities for the cyber security market during the forecast period. Moreover, according to 2019 Cloud Threat report by Oracle and KPMG, due to confusion over shared responsibility security models, 82% cloud users experienced security events. Also, 91% survey respondents were worried about email phishing and 89% were concerned about ransomware threat. In addition, 57% organizations are currently assessing replacing passwords or planning to do so in upcoming 1-2 years, which signifies the lucrative opportunities for the market growth in the future.
The global cyber security market is dominated by key players such as Accenture, Capgemini, Cognizant, HCL Technologies Limited, IBM Corporation, Symantec Corporation, Tata Consultancy Services, Wipro Limited, and others. The key players have adopted various growth strategies to enhance and develop their product portfolio, strengthen their cyber security market share, and to increase their market penetration. For instance, in November 2018, Tata Consultancy Services (TCS) entered into a partnership with ENGIE Laborelec, to protect critical infrastructures against cyber-attacks. In addition, this partnership was mainly focused on developing new products and services to deliver protection against emerging cyber security threats.
The global cybersecurity market size was valued at USD 219 billion in 2023, and is projected to reach USD 578.2 billion by 2033
The global cybersecurity market is projected to grow at a compound annual growth rate of 10.4% from 2024-2033 to reach USD 578.2 billion by 2033
The key players profiled in the reports includes Palo Alto Networks, Microsoft Corporation, Check Point Software Technologies Ltd., Amazon Web Services, Inc., Oracle Corporation, Cisco Systems, Inc., IBM Corporation, Fortinet, Inc., Trend Micro Incorporated, Rapid7, Inc.
Cybersecurity market share was dominated by North America in 2023 and is expected to retain its position during the forecast period
The rise in number of cyber threats drives the cybersecurity market growth owing to the increase in need for organizations to protect sensitive data and ensure the integrity of their digital operations.
Loading Table Of Content...
Loading Research Methodology...



