Hardware Encryption Market Size & Insights:
The global hardware encryption market was valued at USD 293.3 billion in 2022, and is projected to reach USD 1.8 trillion by 2032, growing at a CAGR of 19.5% from 2023 to 2032.
Hardware encryption is a hardware-based technique, which is used for securing digital data. It uses a device with a processor designed specifically to authenticate users and encrypt data. In hardware encryption, security parameters and safeguard keys enhance the performance of encryption. These security parameters protect the encryption from cold boots and brute-force attacks. The major advantage of hardware encryption is its independence from the host computer's operating system, ensuring that data remains secure, even in cases where the operating system (OS) is compromised.

Factors such as the increase in regulatory compliances regarding protection of privacy and sensitive records and reduction in prices of hardware encryption equipment’s majorly drive the growth of the market. Moreover, growth in concern related to data security and privacy, rise in penetration of consumer electronics, are anticipated to drive the growth of the hardware encryption industry during the forecast period. For instance, in September 2023, Arqit Quantum Inc. a leader in quantum-safe encryption, launched of its third application product, “Arqit WalletSecure™”. The WalletSecure™ makes any Ethereum-based digital wallet used to store and transact digital asset transactions quantum-safe. Furthermore, the rise in adoption of Internet of Things (IoT) technology and cloud services as well as technological advancements in encryption chips are anticipated to provide lucrative opportunities for market expansion during the forecast period. However, high capital investment and limited use of encrypted devices across some of the countries may hinder the hardware encryption market growth.
Key Takeaways:
- By product, the hard disk drive (HDD) segment accounted for the largest hardware encryption market share in 2022.
- By algorithm standard, the RSA segment accounted for the largest hardware encryption market share in 2022.
- By architecture, the ASIC segment accounted for the largest hardware encryption market share in 2022.
- Based on application, the consumer electronics segment accounted for the largest hardware encryption market share in 2022.
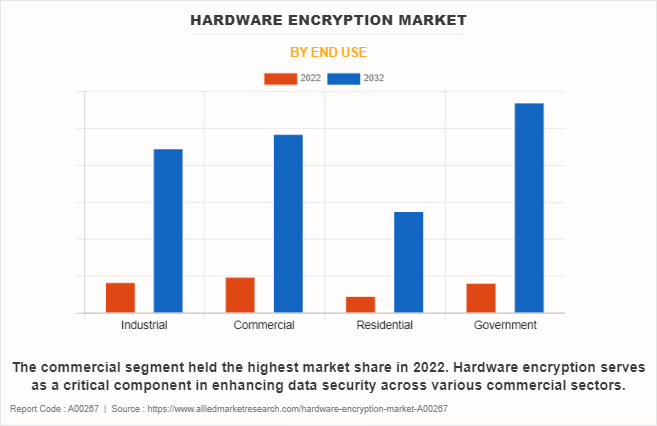
- Depending on end use, the commercial segment accounted for the largest hardware encryption market share in 2022.
- Region wise, North America generated the highest revenue in 2022.
Segment Review:
The hardware encryption market is segmented into algorithm standard, architecture, product, application, end use, and region. Depending on algorithm standard, the market is segregated into RSA, AES, and others. By architecture, it is classified into ASIC and FPGA. By product, the market is divided into hard disk drive (HDD), solid state drive (SSD), universal serial bus (USB), and incline network encryptor. By application, the market is categorized into consumer electronics, IT & telecom, automotive & transportation, aerospace & defense, healthcare, government & public utilities, BFSI, and others. By end use, the market is fragmented into industrial, commercial, residential, and government. Region wise, the market is analyzed across North America, Europe, Asia-Pacific, and LAMEA.
On the basis of end use, the commercial segment dominated the hardware encryption market size in 2022 and is expected to maintain its dominance in the upcoming years. This sector deals with sensitive financial transactions, vast data networks, and consumer information, hardware encryption provides a robust solution to protect against cyber threats and ensure data integrity. However, the government segment is expected to witness the highest growth in the upcoming years. The adoption of hardware encryption in the government sector contributes to national security efforts, protects against cyber threats, and ensures the confidentiality of data vital for effective governance.
Region-wise, Asia-Pacific is dominated the market share in 2022 for the hardware encryption market expected to exhibit the highest growth during the forecast period, owing to the growth of digitalization and increase in investment in advanced technologies such as AI, ML, and cloud computing in the region. For instance, in May 2020, For instance, in June 2023, DataLocker, the leading provider of encryption solution, offered SafeConsole® central management services and encrypted storage solutions to governments, military organizations, and enterprises in over 40 countries. The company's unwavering commitment to security and trust is exemplified by its adherence to the highest industry standard.
Competition Analysis:
The market players operating in the hardware encryption market are Broadcom Inc., International Business Machines Corporation, McAfee, LLC, Micron Technology, Inc., NetApp, Inc., Samsung Electronics Co., Ltd., Toshiba Corporation, Kingston Technology Company, Inc., Seagate Technology, LLC. And Western Digital Technologies, Inc. These major players have adopted various key development strategies such as business expansion, new product launches, and partnerships, which help to drive the growth of the hardware encryption industry globally.
Recent Product Launch in the Hardware Encryption Market
In September 2023, Kingston Digital, Inc., the world leader in memory products and technology solutions, launched the best-in-class Kingston IronKey D500S, hardware-encrypted USB flash drive, that will provide military-grade security for classified data in transit.
In February 2023, IBM Corporation launched the IBM Hyper Protect Crypto services for AIX and Linux on IBM power systems vrtual server. Through this development, organizations can use IBM Power Systems Virtual Server to expand their on-premises servers to modern-day hybrid cloud infrastructures, helping them to smoothly move and manage their workloads across cloud and on-premises environments.
Recent Partnership in the hardware encryption Market
In September 2022, Telefonica Technology, partnered with McAfee Corporation, the world leader in online protection, to integrate the American company's online protection products into its portfolio and strengthen its cybersecurity value proposition aimed at the self-employed and consumers in EMEA (Europe, Middle East and Africa) and Latin America.
Top Impacting Factors:
Upsurge in penetration of consumer electronics such as smartphones and tablets
The hardware encryption market has witnessed a notable upsurge due to the widespread penetration of consumer electronics, particularly smartphones and tablets. As these devices play an essential role in everyday activities, handling extensive amounts of personal and sensitive data there is a surge in acknowledgment of the necessity for strong security measures.
Consumers and businesses alike are seeking effective ways to protect confidential information, including financial transactions, personal communications, and sensitive documents, stored on these devices. Hardware encryption provides a compelling solution by integrating dedicated cryptographic processors or modules within these electronic devices, offering an added layer of security beyond traditional software-based methods. This surge in consumer electronics adoption has consequently driven the demand for hardware encryption, as users prioritize safeguarding their data against potential cyber threats and unauthorized access, thereby propelling the hardware encryption market forecast.
Key Benefits For Stakeholders
- This report provides a quantitative analysis of the market segments, current trends, estimations, and dynamics of the hardware encryption market analysis from 2022 to 2032 to identify the prevailing hardware encryption market opportunities.
- The market research is offered along with information related to key drivers, restraints, and opportunities.
- Porter's five forces analysis highlights the potency of buyers and suppliers to enable stakeholders make profit-oriented business decisions and strengthen their supplier-buyer network.
- In-depth analysis of the hardware encryption market segmentation assists to determine the prevailing market opportunities.
- Major countries in each region are mapped according to their revenue contribution to the global market.
- Market player positioning facilitates benchmarking and provides a clear understanding of the present position of the market players.
- The report includes the analysis of the regional as well as global hardware encryption market trends, key players, market segments, application areas, and market growth strategies.
Hardware Encryption Market Report Highlights
| Aspects | Details |
| Market Size By 2032 | USD 1.8 trillion |
| Growth Rate | CAGR of 19.5% |
| Forecast period | 2022 - 2032 |
| Report Pages | 446 |
| By Product |
|
| By Algorithm Standard |
|
| By Architecture |
|
| By Application |
|
| By End Use |
|
| By Region |
|
| Key Market Players | Kingston Technology Company, Inc., International Business Machines Corporation, NetApp, Inc., Seagate Technology LLC, McAfee, LLC, Western Digital Technologies, Inc., Toshiba Corporation, Broadcom Inc., Micron Technology, Inc., Samsung Electronics Co., Ltd. |
Analyst Review
The adoption of hardware encryption has increased for protecting sensitive data on portable devices such as USB flash drives and laptops. Numerous benefits provided by hardware encryption technology such as consistent performance, ease of use, and robust protection against common sophisticated attacks offset its cost higher. For instance, Trend Micro™ Endpoint Encryption encrypts data on a wide range of devices both PCs and Macs, laptops and desktops, USB drives, and other removable media. This solution combines enterprise-wide full disk, file/folder, and removable media encryption to prevent unauthorized access and use of private information. A single, well-integrated management console allows businesses to manage users holistically using the same console for endpoint protection and other Trend Micro security products. Deploying Trend Micro Endpoint Encryption ensures that data will continue to be protected as the mobile computing devices and organizational needs change.
Furthermore, today, enterprises and service providers are increasingly using network functions virtualization (NFV) and software-defined networking (SDN) technologies to design, deploy and manage their networks and cloud-based services. These software-based technologies provide organizations cost and operational benefits as they move network functions from dedicated network encryption hardware appliances to virtual servers. However, these technologies can also present additional security challenges for protecting sensitive data that runs across these networks due to their virtualized architecture. Owing to this reason, more organizations are embracing the advantages of virtualized networks to deliver cost-effective scalability, flexibility, and network management to the network edge. For instance, Gemalto, the world leader in digital security, launched of a virtualized network encryption platform redefines network data security by providing the crypto agility required to ensure sensitive data and transmissions remain secure, regardless of network design.
Such enhanced factors are expected to provide lucrative opportunities for the hardware encryption market growth during the forecast period. Nevertheless, the hardware encryption market is consolidated and competitive, owing to the presence of well-diversified regional and international vendors. Prominent strategies such as product launch and acquisition are adopted by leading companies to expand their product offerings. For instance, May 2022, Kingston Digital, Inc., a world leader in memory products and technology solutions, released the newest addition to its encrypted lineup, IronKey Vault Privacy 80 External SSD (VP80ES).
This marks Kingston’s first innovative OS independent external SSD with touchscreen and hardware-encryption for data protection. Furthermore, VP80ES is designed to protect data while also being user-friendly. The drive is ideal to safeguard against brute force attacks and BadUSB with digitally signed firmware for users from small-to-medium businesses (SMB) to content creators. It is military-grade security measures that make it superior over the internet and cloud services for securing important company information, documents, or high-res images and videos. Such developments are anticipated to provide lucrative opportunities for market growth in the coming years.
The North America is the largest market for the Hardware Encryption.
Hardware Encryption Market to Reach $1,764.42 Billion, by 2032
Factors such as increase in regulatory compliances regarding protection of privacy & sensitive data and reduction in prices of hardware encryption devices majorly drive the growth of the global hardware encryption market.
The key growth strategies for Hardware Encryption include product portfolio expansion, acquisition, partnership, merger, and others.
The market players operating in the hardware encryption market are Broadcom Inc., International Business Machines Corporation, McAfee, LLC, Micron Technology, Inc., NetApp, Inc., Samsung Electronics Co., Ltd., and others
Loading Table Of Content...
Loading Research Methodology...



