Mobile Security Market Size & Share:
The global mobile security market was valued at USD 3.3 billion in 2020, and is projected to reach USD 22.1 billion by 2030, growing at a CAGR of 21.1% from 2021 to 2030.
Increase in online mobile payment and rise in security need from adoption of bring your own devices (BYOD) in workplaces are the major factors that drive the growth of the market. In addition, surge in need to provide phone security to video streaming content fuels the growth of the market. Furthermore, high cost of mobile security solution and complexity in designing embedded security solution hampers the growth of the market. Furthermore, growth in usage of machine learning and artificial intelligence in phone security application is expected to provide lucrative opportunity for the market.
Mobile security is one of the key elements within mobile devices as it provides better security function to smartphones, laptop, and tablets. In addition, increase in usage of mobile devices for tasks that involve sensitive data such as important banking information, credit card numbers, and social security numbers boosts the growth of the market.
The report focuses on growth prospects, restraints, and trends of the mobile security market analysis. The study provides Porter’s five forces analysis to understand the impact of various factors, such as bargaining power of suppliers, competitive intensity of competitors, threat of new entrants, threat of substitutes, and bargaining power of buyers, on the mobile security market.
Segment Review:
The global mobile security market is segmented on the basis of operating system, end user, enterprise solution type, organization size and industry vertical. In terms of operating system, the market is divided into android, iOS and others. By end user, it is bifurcated into enterprises and individuals. In terms of enterprise solution type, it is segmented into authentication, mobile application security, mobile data protection, and others. As per organization size the market is classified into large enterprises and small & medium enterprises. Based on industry vertical, the market is bifurcated into BFSI, IT & telecom, retail & e-commerce, healthcare, government & defense and others. Region wise, it is analyzed across North America, Europe, Asia-Pacific, and LAMEA.
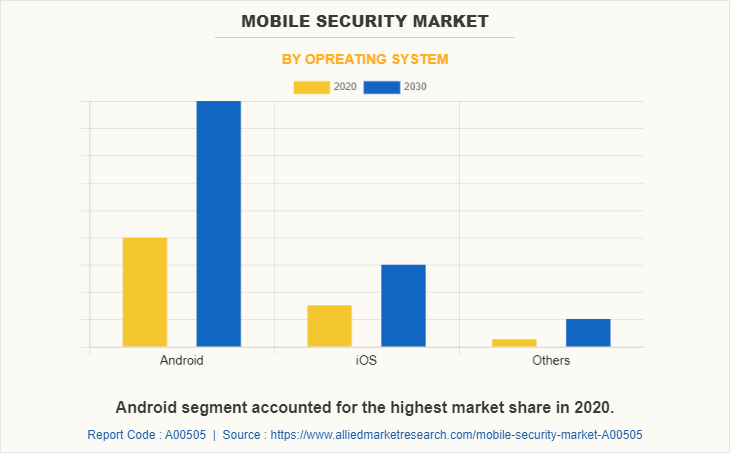
According to operating systems, the android segment holds the largest mobile security market share, since, android has emerged to be one of the most adaptive operating system because of the efficient working and application appearance in the mobile security market. However, the others segment is expected to grow at the highest rate during the forecast period, since the operating system of windows and Blackberry provides secured multitasking and supports specialized input devices that have been adopted for use in BlackBerry handhelds, particularly trackpad, trackball, track wheel, and recently the touchscreen. BlackBerry OS is a closed operating system that itself acts as a security tool for smartphone users.

Region-wise, the mobile security market share was dominated by North America in 2020, and is expected to retain its position during the forecast period. This is attributed to the adoption of the mobile technologies in North American businesses is propelled by varied factors such as technological advances, availability, cost, societal trends and economics. However, Asia-Pacific is expected to witness significant growth during the forecast period, owing to the demand for mobile device and mobile application management is growing exponentially in the Asia-Pacific region and this need spans all the industries.
The key players profiled in the mobile security market analysis are Apple Inc., BlackBerry Limited, Broadcom Inc., Citrix Systems, Inc., Google LLC, International Business Machine Corporation, Mobileiron, Inc., Microsoft Corporation, Samsung Electronics Co. Ltd., and VMware, Inc.
Top Impacting Factors:
Rise in Security Need due to Rise in Adoption of BYOD in Workplaces
Companies and enterprises are adopting the BYOD trend, which creates a much efficient workplace for employees. The employees use the network of the company, not only in work hours but also when the device is out of the company’s premises. Thereby, the need to ensure safety and security of financial and corporate data at remote locations increases. The security solution adopted by companies should differentiate between the personal data of employees and company’s data. Individual users also face data loss when hackers target the payment details, audio, and video files of the users. The need for mobile security solutions is increasingly becoming a necessity for all the mobile users to protect their data.
Growth in Usage of Machine Learning and Artificial Intelligence in Mobile Security Application
Artificial intelligence is an integral part of different smart phones and their development. Smart phone manufacturers, such as Apple, Samsung, Huawei, and others, leverage machine learning and artificial intelligence into the development of their smartphone models, thus, providing lucrative opportunities for the growth of the mobile security market.
Furthermore, according to a study, 200 mobile security application companies are expected to include AI artificial intelligence and machine learning in smartphones to improve various features, such as camera and security applications. Moreover, companies are implementing artificial intelligence in smartphones and tablets for empowering mobile applications and increasing the performance of various mobile devices. In addition, AI allows mobile applications to get insights from various data generated by all users and helps improve decision making capabilities of the user. Thus, proving to be a lucrative opportunity for the mobile security industry.
Regional Insights:
North America:
North America leads the mobile security market due to the high penetration of mobile devices, the rising incidence of cyber-attacks, and stringent regulatory requirements around data protection. The United States is a key driver of this market, with businesses and individuals heavily relying on mobile devices for day-to-day operations. The demand for mobile security is further boosted by regulations like the California Consumer Privacy Act (CCPA) and industry standards such as HIPAA in healthcare, which mandate the protection of sensitive information. Canada also contributes to market growth, with increasing investments in mobile security by government and private organizations.
Europe:
Europe is another significant market for mobile security, driven by strong data protection regulations such as the General Data Protection Regulation (GDPR). Countries like Germany, France, and the UK are leading in the adoption of mobile security solutions as companies prioritize protecting mobile data against potential breaches. The region’s focus on privacy and security in digital transactions has encouraged both businesses and individuals to adopt mobile security solutions. Additionally, the rising number of mobile users and an increase in e-commerce activities across Europe have pushed the demand for advanced security measures.
Asia-Pacific:
The Asia-Pacific region is experiencing rapid growth in the mobile security market, fueled by the widespread use of smartphones and increasing internet penetration. Countries like China, India, Japan, and South Korea are at the forefront of this growth. China and India have seen a surge in mobile commerce and online banking, making mobile security essential to protect financial transactions. The growth of 5G technology in South Korea and Japan has also driven demand for more robust mobile security solutions to ensure secure connectivity and data protection in enterprise environments.
Latin America:
Latin America is witnessing a growing mobile security market, particularly in countries like Brazil and Mexico, where mobile phone usage is rapidly increasing. The region faces rising cyber threats, prompting businesses to invest in mobile security to safeguard personal and corporate data. Mobile banking and e-commerce are becoming more prominent in the region, leading to the adoption of security solutions to protect against fraud and unauthorized access. However, challenges such as limited cybersecurity infrastructure and budget constraints may slow the market's growth.
Middle East & Africa:
The Middle East & Africa region is gradually adopting mobile security technologies, with UAE and Saudi Arabia being early adopters in the Middle East. Government initiatives aimed at promoting digital transformation, along with the growing reliance on mobile phones for business and personal use, are contributing to the demand for mobile security. In Africa, the increasing use of mobile payments and internet services is driving the need for mobile security solutions, though market adoption is still in its early stages.
Key Industry Developments:
April 2024: McAfee launched its new mobile security platform focusing on AI-driven threat detection to prevent malware and phishing attacks on mobile devices in North America. This solution targets enterprise users to ensure data protection in remote working environments.
December 2023: Kaspersky announced a partnership with Telefónica in Europe to integrate its mobile security solution into the telecom operator’s services, providing enhanced security for customers against phishing and data breaches.
October 2023: Zimperium, a mobile security provider, expanded its operations in the Asia-Pacific region, focusing on providing mobile threat detection and response solutions to enterprises in Japan and South Korea. The company is targeting financial services and healthcare sectors where mobile data security is critical.
August 2023: Trend Micro introduced its Mobile Security-as-a-Service platform in Latin America, offering cloud-based protection against emerging mobile threats for enterprises in Brazil and Mexico. This service is expected to enhance mobile security for the region's growing mobile workforce.
June 2023: BlackBerry launched a new mobile security software suite aimed at securing enterprise mobile applications in Europe. The platform provides end-to-end encryption for sensitive data and secure communication between employees using mobile devices.
Key Benefits for Stakeholders:
- This report provides a quantitative analysis of the market segments, current trends, estimations, and dynamics of the mobile security market analysis from 2020 to 2030 to identify the prevailing mobile security market forecast.
- The mobile security market research is offered along with information related to key drivers, restraints, and opportunities.
- Porter's five forces analysis highlights the potency of buyers and suppliers to enable stakeholders make profit-oriented business decisions and strengthen their supplier-buyer network.
- In-depth analysis of the mobile security market segmentation assists to determine the prevailing market opportunities.
- Major countries in each region are mapped according to their revenue contribution to the global mobile security market size.
- Market player positioning facilitates benchmarking and provides a clear understanding of the present position of the market players.
- The report includes the analysis of the regional as well as global mobile security market trends, key players, market segments, application areas, and market growth strategies.
- The quantitative analysis of the global mobile security market size from 2021 to 2030 is provided to determine the market potential.
Mobile Security Market Report Highlights
| Aspects | Details |
| By Opreating System |
|
| By End User |
|
| By Region |
|
| Key Market Players | IBM Corporation, BlackBerry Limited, Google LLC, MobileIron, Inc., Apple Inc., Broadcom Inc., Samsung Electronics Co. Ltd, VMware, Inc., Microsoft Corporation, Citrix Systems, Inc. |
Analyst Review
The adoption of mobile security has increased over time due to rise in adoption of smart phones and mobile devices in various different industries and growth in sales of smartphones. In addition, the ability of software to protect the confidentiality of digital data stored on mobile devices or transmitted over the internet increases its popularity among end users. Furthermore, technological advancements and increase in awareness amongst consumers can lead to a rapid growth during the forecast period.
Furthermore, increase in economic strength of developing nations, such as China and India, is expected to provide lucrative opportunities for the market growth. North America is expected to dominate the market during the forecast period. Moreover, emerging countries in Asia-Pacific and Latin America are projected to offer significant growth opportunities during the forecast period. The global players are focusing toward product development and increase their geographical presence, owing to growth in competition among local vendors, in terms of features, quality, and price. In addition, these players are adopting various business strategies to enhance their product offerings and strengthen their foothold in the market. For instance, in December 2019, IBM Corporation partnered with Vodafone & Idea to launch a secure device manager platform to secure emails and protect devices containing company data used for automating the field sales force. Some of the key players profiled in the report include Apple Inc., BlackBerry Limited, Broadcom Inc., Citrix Systems, Inc., Google LLC, IBM Corporation, Mobileiron, Inc., Microsoft Corporation, Samsung Electronics Co. Ltd., and VMware, Inc. These players have adopted various strategies to increase their market penetration and strengthen their position in the industry.
The Mobile Security Market is estimated to grow at a CAGR of 21.1% from 2021 to 2030
The Mobile Security Market is projected to reach $22.07 billion by 2030.
North America dominated global mobile security market in 2020.
The key players profiled in the mobile security market analysis are Apple Inc., BlackBerry Limited, Broadcom Inc., Citrix Systems, Inc., Google LLC, International Business Machine Corporation, Mobileiron, Inc., Microsoft Corporation, Samsung Electronics Co. Ltd., and VMware, Inc.
The key growth strategies of Mobile Security market players include product portfolio expansion, mergers & acquisitions, agreements, geographical expansion, and collaborations.
Loading Table Of Content...



