Lawful Interception Market Statistics, 2031
The global lawful interception market was valued at $3.4 billion in 2021, and is projected to reach $29.9 billion by 2031, growing at a CAGR of 24.7% from 2022 to 2031.
Lawful interception is a procedure for gaining access to a private communication network that is allowed by the courts. This service is used by a variety of government agencies and network providers to hunt down criminals and prevent crimes. The income in this report is derived from the selling of hardware, software, and lawful interception services for the implementation of lawful interception. Revenues from unlawful interception operations were not taken into account in this report. Various communication modalities, including audio–video calls, text messages, fax, digital images, downloaded data, and files sent over the internet are intercepted via lawful interception.

Increase in demand for monitoring, tracking data of players, surge in demand for chatbots & virtual assistants to interact with followers boost the growth of the global lawful interception market. In addition, increase in demand for real-time data analytics positively impacts the lawful interception market growth. However, lack of trained & skilled professionals and high implementation & maintenance cost hamper the lawful interception market growth. On the contrary, increase in demand for AI for making future predictions is expected to offer remunerative opportunities for expansion of the lawful interception industry during the forecast period. The lawful interception market is segmented into Solutions, Network Technology, Communication Technology and End User.
Key Market Segment:
The global lawful interception market is segmented into solution, network technology, communication technology, end user, and region. Depending on solution, the market is segmented into devices, software, and services. On the basis of network technology, the market is fragmented into VoIP, WLAN, WiMAX, DSL, PSTN, ISDN, mobile voice telephony, mobile data, and others. By communication technology, it is segregated into voice communication, video, text messaging, facsimile, digital pictures, data downloads, and file transfer. As per end user, it is classified into government and enterprises. Region wise, it is analyzed across North America, Europe, Asia-Pacific, and LAMEA.
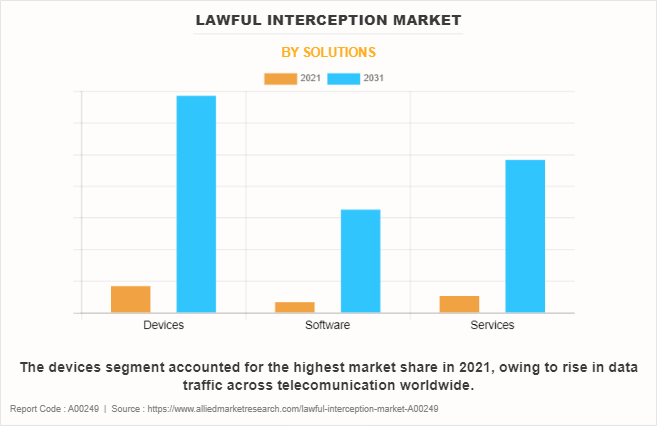
In terms of solution, the devices segment holds the highest lawful interception market share. This is atributed to the rise in data traffic across telecommunication networks worldwide. However, the software segment is expected to grow at the highest rate during the forecast period, owing to increase in number of skilled workforce and need of maintaining the security and working of the software.
Region wise, the lawful interception market size was dominated by North America in 2020, and is expected to retain its position during the forecast period, owing to abundance of lawful interception solutions vendors such as Cisco, FireEye, thus aiding the growth of the lawful interception market. However, Asia-Pacific is expected to witness significant growth during the forecast period, owing to increase in adoption of efficient telecommunication technologies in countries such as Japan, Korea, and China that has led to an upsurge in data-based communication.
The key players operating in the global lawful interception market analysis include AQSACOM Innovating Intelligence, BAE Systems, Cisco Systems, Inc., Fire Eye, Incognito software system Inc., JSI Telecom, NICE Systems, SS8 Incorporation, Siemens AG, and Utimaco GmbH. These players have adopted various strategies to increase their market penetration and strengthen their position in the lawful interception industry.
Top Impacting Factors
Rise in Number of Criminal Activities
The necessity for technologically sophisticated crime detection technologies and favourable lawful interception legislation has grown as the number of criminal and terrorist activities throughout the world have increased. Law enforcement and intelligence organisations employ lawful interception to study suspects' communication data to combat and control crimes such as terrorism, domestic crimes, and cybercrime. Network operators and service providers transfer the suspect's intercepted data to intelligence agencies and further, the legal authority issues a warrant. To track and monitor illegal actions, the monitoring centres evaluate forensic telecommunication data collected from service providers (SPs) and internet service providers (ISPs) to extract general information for law enforcement authorities regarding the suspect's groups, activities, and associations.
Rise in Volume of Data Traffic and Security Threats
Communication channel traffic has increased at an exponential rate. The expansion of data traffic will be fueled by increasing use of smartphones, particularly in Asian countries. Voice over Internet Protocol (VoIP) is now able to allow voice calls in offices. Individual consumers prefer data-based services to traditional phone or mobile voice calls for communication. The exponential expansion in packet data volume has resulted in an increase in the frequency of cybercrimes and data breaches. To protect national security, the government and other organisations use cyber data interception. As a result, increase in data traffic and security concerns are two main drivers propelling the lawful interception market industry.
Digital Capabilities:
With the Increasing advancements in cloud computing, the concept of virtualization is gaining traction across the globe. The virtualization of modern data centers improves virtual network security, enabling vendors to offer cloud-based interception solutions and connect cybernetic traffic to physical monitoring tools. In addition, the developments in data-based communications have led to the expansion of telecommunication networks, which is contributing to the global lawful interception market growth. Furthermore, mobile phone tracking systems are also being set up to assist security agencies in protecting and preserving consumer interest. In addition, governments of both developed and emerging nations are rapidly adopting lawful interception to monitor and decrypt digital and analog information. Moreover, various companies are involving in the research and development of cloud-based interception solutions.
For instance, in January 2020, AQSACOM delivers ALIS, a Lawful Cyber Intelligence System, to virtualized network function architectures. It is deployed as a software-based solution and can be readily integrated into any virtualized network. Moreover, the increasing digitalization and the rapid adoption of communication devices, including smartphones and tablets, have taken businesses and connectivity among people to an advanced level. Such advances have also provided an impetus to increasing illegal online activities. As a result, law enforcement and intelligence agencies are focusing on investigating terrorist networks, criminal operations, drug trafficking, financial crimes, and other illegal activities worldwide.
Moreover, the implementation of favorable government policies for the periodic monitoring and controlling of illicit activities across numerous communication systems further prompts the market. Advanced technologies such as Voice over IP (VoIP) and wireless, have enabled the mobility of users by increasing the scope for unlawful activities and generating a huge amount of data traffic and security threats. This result in actuating the existing demand for lawful interception in telecom service companies, ISPs, Network operators, and SPs for lawfully locating, intercepting, monitoring, and analyzing wired and wireless communication.
Key Benefits
Lawful interception (LI) is a legally approved surveillance of telecommunication services for investigating and prosecuting criminal activities and terrorist operations. It is a tool used by law enforcement and intelligence agencies (LEAs) to identify, monitor, and deliver electronic communication to individuals. It also enables the interception of communication traffic for a specific user. Furthermore, organizations from different end-use industries are relying on a lawful interception to protect against malicious network traffic. Moreover, advanced network technologies are expected to offer significant opportunities for growth in the market in the coming time. In various developed countries, lawful interception is mandated for national security and real-time surveillance. Administrations of several nations are taking initiatives to update the laws of lawful interception and optimize the regulation process, which can monitor illegal activities across communication systems.
Government Regulations:
All well-governed IT industries should be able to demonstrate due diligence to ensure regulatory compliance in applicable fields, including IT. Organizations are adopting to manage, store, and extract relevant and useful information from the data stored. For instance, California’s Online Protection Privacy Act provides explicit privacy rights and allows users to know how their information will be used in the future. Furthermore, cloud security regulations are strongly adhered to by almost all big data service providers to operate as global service providers, for instance, the U.S. security regulation is mandatory to be adhered to by the majority of players located in this country.
In addition, the Implementation of favorable laws for lawful interception by various governments is projected to benefit the market in the coming time. For instance, Communications Assistance for Law Enforcement Act (CALEA) is one of the laws that features LI standards in the United States. Further, The European Telecommunication Standards Institute (ETSI) and the Third Generation Partnership Project (3GPP) have led the way in standardization. International cooperation between various European countries, New Zealand, Canada, Australia, Canada, and the U.S. have played a significant role in strengthening the LI standards. Owing to the aforementioned factors, the market is expected to flourish in the coming period.
For instance, Facebook sued an Israeli technology firm, NSO Group, owing to an allegation that NSO’s spyware, Pegasus was being used to spy on Facebook’s messaging platform. In July 2021, it was reported that the malware was used illegally to spy on Indian journalists, ministers, activists, and members of the opposition party. Having such instances of cybercrime, the market for law interception is projected to strengthen notably in the forthcoming tenure.
Key Benefits for Stakeholders:
The study provides an in-depth analysis of the global lawful interception market forecast along with current & future trends to explain the imminent investment pockets.
Information about key drivers, restraints, & opportunities and their impact analysis on global lawful interception market trends is provided in the report.
The Porter’s five forces analysis illustrates the potency of the buyers and suppliers operating in the industry.
The quantitative forecast of the lawful interception market analysis size from 2021 to 2030 is provided to determine the market potential.
Lawful Interception Market Report Highlights
| Aspects | Details |
| Market Size By 2031 | USD 29.9 billion |
| Growth Rate | CAGR of 24.7% |
| Forecast period | 2021 - 2031 |
| Report Pages | 283 |
| By Solutions |
|
| By Network Technology |
|
| By Communication Technology |
|
| By End User |
|
| By Region |
|
| Key Market Players | JSI Telecom, NICE Ltd., SIEMENS AG, BAE SYSTEMS, INCOGNITO SOFTWARE, CISCO SYSTEMS, INC., AQSACOM, FireEye, Inc., Utimaco GmbH, SS8 NETWORKS, INC. |
Analyst Review
Lawful interception is a strong security tool for combating crime and upholding the rule of law. In nations without set interception standards, the government and other regulatory authorities might utilize interceptions to spy on its inhabitants, which would be a breach of privacy. Network operators are not compelled to conduct legitimate interception for law enforcement agencies (LEAs) in nations, where no laws for lawful interception have been created. Local operators, on the other hand, would be forced to do so by the ruling government's influence and authority. As a result, it is critical to put in place legal Lawful interception practices everywhere across the globe.
The key providers of lawful interception market such as Utimaco GmbH, SS8 Networks Inc., and FireEye account for a significant share in the market. With larger requirement for lawful interception, various companies are partnering to improve the surveillance industry. For instance, in August 2021, IT security solution provider, Utimaco and achelos GmbH, a manufacturer-independent software development and consulting firm, have further extended their longstanding cooperation with a partnership contract. Accordingly, achelos GmbH is now marketing all products and solutions from the Utimaco portfolio as a value-added reseller. The partnership helped Utimaco to implement their own customer-specific development projects for HSM firmware, develop solutions based on this and act as a value-added reseller for Utimaco's HSM.
In addition, with increase in demand for lawful interception services, various organizations are expanding their current services to meet the rising demand. For instance, in September 2020, BAE Systems, a leading provider of Lawful Intercept (LI) solutions ,globally, developed world’s first standards based 5G Stand Alone Lawful Interception solution. Lawful interception solutions enable CSPs to share communications data for investigatory purposes, which is vital to law enforcement and national security agencies. Regulated by law, interception data forms a key element in national efforts to monitor threats, detect & deter crimes, and investigate & prosecute criminals. Online and connected devices are slated to take a giant leap with 5G, increasing the risk of cybercrime and exploitation of new technology by criminals.
The CXOs further added that market players are expanding their business operations and customers by increasing their acquisition. For instance, in June 2021, SS8 Networks, a leader in lawful intercept and monitoring center platforms, announced an agreement to acquire the assets of Bivio Networks, Inc. Bivio is a developer of innovative, high-performance network security platforms for federal and commercial network operators. The investment represents SS8’s ongoing commitment to rapidly innovate their Xcipio family of products. The acquisition will help implementation of Bivio’s OS into Xcipio’s sensor and mediation platform, which will significantly enhance the scalability and increase the number of applications that can be managed. The result will be a mediation and interception platform that delivers promising performance and flexibility.
The lawful interception market is estimated to grow at a CAGR of 24.7% from 2022 to 2031.
The lawful interception market is projected to reach $ 13,717. 85 million by 2031.
Increase in demand for monitoring, tracking data of players, surge in demand for chatbots& virtual assistants to interact with followers boost the growth of the global lawful interception market. In addition, increase in demand for real-time data analytics positively impacts the lawful interception market growth.
The key players profiled in the report include AQSACOM Innovating Intelligence, BAE Systems, Cisco Systems, Inc., Fire Eye, Incognito software system Inc., JSI Telecom, NICE Systems, SS8 Incorporation, Siemens AG, and Utimaco GmbH.
The key growth strategies of lawful interception market players include product portfolio expansion, mergers & acquisitions, agreements, geographical expansion, and collaborations.
Loading Table Of Content...
Loading Research Methodology...



